Secure Telephone Units, Crypto Key Generators,
Encryption Equipment, and Scramblers

Secure Telephone Units, Crypto Key Generators,
Encryption Equipment, and Scramblers
Granite Island Group provides a broad spectrum of information security protection protecting information transmission in a variety of mediums for the U.S. Government, local law enforcement agencies, banks, universities, multinational corporations and foreign governments.
Products and Services
Products and services range from desktop secure phones and data modems, to fax encryptors and secure video.
Secure transmissions; whether telephone conversations, facsimile (fax) copies, or automated information systems (AIS) communications have long been possible through encryption, but for many years the equipment was bulky, complex, and expensive. In the 1960s the KY-3, one of the first practical voice encryption devices, came on the market (which was the size of a short refrigerator or fat two drawer filing cabinet). In 1970, the Secure Telephone Unit, First Generation or STU-I was launched, followed in 1975 by the STU-II, which mustered some 10,000 users.
In 1984, the National Security Agency (NSA) initiated the Future Secure Voice System (FSVS), an aggressive, accelerated program to button up US voice communications by the end of the 1980s. In fact, the Secure Telephone Unit, Third Generation (STU-III) was developed and produced by 1987. To ensure widespread use, the STU-III was designed to be about the size of a conventional telephone desk set, user-friendly, and relatively low-cost.
It should however, be pointed out that legitimate encryption products are not inexpensive or easy to obtain, and you can expect to pay several thousand dollars for even the most basic equipment.
What began in 1985 as a small project responding to a U.S. Government initiative to secure all classified and sensitive information, the STU-III program, has blossomed into a strong global organization which is recognized worldwide as an innovative leader in communications security.
The Secure Telephone Unit - Third Generation (STU-III) is a low-cost, user-friendly, secure telephone device. The terminals are designed to operate reliably, with high voice quality, as both ordinary telephones and secure instruments over the dial-up public switch telephone network. STU-III operates in full-duplex over a single telephone circuit using echo canceling modem technology. STU-IIIs come equipped with 2.4 and 4.8 kbps code-excited linear prediction (CELP) secure voice. Secure data can be transmitted at speeds of 2.4, 4.8, and 9.6 kbps. The data throughput between two STU-IIIs can only be as great as the slowest STU-III connected. The STU-III Family consists of some of the following devices:
The STU-III/Low Cost Terminal (LCT) was designed for use in the office environment among a broad spectrum of military, civil, government, and selected private sector users. It is compatible with standard modular or multiline (key system) connectors and operates full-duplex over a single telephone circuit.
The STU-III/Cellular Telephone is interoperable with all other versions of the STU-III Family. It combines cellular mobile radio-telephone technology with advanced secure voice/data communications. The unit includes a message center that is integrated with the standard cellular handset; it can be conveniently mounted inside a vehicle and provides all STU-III functions, including authentication/classification display. It provides end-to-end security over a commercial cellular network and will operate in all continental US (CONUS) and many foreign cellular telephone systems.
The STU-III/Allied (A) is a specialized version of the STU-III/LCT that is compatible with the STU-II. It retains all basic STU-III functions and capabilities and incorporates STU-II BELLFIELD KDC, STU-II net, and STU-II multipoint modes of operation.
The STU-III/Remote Control Interface (R or RCU) provides RED enclave subscribers with STU-III compatible secure communications in a rack-mounted, remotely controlled, line encrypting unit. When used in conjunction with a RED switch or conferencing director, the STU-III/R allows STU-III users to confer with multiple STU-III users or others who have secure functions. It is capable of encrypting/decrypting voice or data over two-wire or four-wire telephone systems and incorporating a 2.4 kbps BLACK digital (external modem) interface.
The MultiMedia Terminal (MMT) 1500 is a diversified STU-III capable of clear or secure voice and data communications over both analog and digital mediums. The MMT interfaces to the commercial telephone system via a standard RJ-11 telephone jack and to digital systems through a Black Digital Interface (BDI). The BDI port will support both half-and full-duplex communications, precedence dialing, black digital network signaling, and multiple satellite hops. When unattended the MMT can automatically answer an inbound call without operator intervention and establish a secure link with any user on a preprogrammed Access Control List (ACL).
The Inter Working Function (IWF) is the shore gateway device that provides the digital to analog conversion between the MMT and the analog STU-III. The IWF supports half and full duplex voice and data communications with rates of 2.4, 4.8, and 9.6Kbps. The IWF improves secure voice and data synchronization over multiple satellite hops with programmable extended time-outs and pre-staging of STU-III call information. The IWF supports all necessary network-signaling functions to enable call setup and status messages including canned voice messaging to the analog user.
The STU-III Secure Data Device (SDD) is designed with the same capabilities as other members of the STU-III family including Secure Access Control System (SACS), remote authentication (RA), remote control, auto-answer secure data, and capable of operating in both attended and unattended environments. The SDD provides protection for facsimiles, e-mail, and computer communications.
The Motorola CipherTAC 2000 (CTAC) STU-III family compatible secure voice communications via cellular phone. CTAC without an inserted CipherTAC 2000 security module is unclassified and functions as a non-secure commercial off the shelf (COTS) telephone product. The CTAC Ciphertac security module is certified for all levels of classified discussions up to and including SECRET in an adequate operating/security environment.
The "keying stream" is a polymorphic regenerating mathematic algorithm which takes a initialization key and mathematically morphs it into a bit stream pattern. The "keying stream" is created by the "Key Generator" and is the actual heart of the STU. A portion of the "keying stream" are then mixed back into to the original key, and process repeated. The results is a pseudo-random bit stream that if properly implemented is extremely difficult (but not impossible) to decrypt.
Even the most sophisticated cryptographic algorithm can be easily expressed in the form of a simple equation in boolean algebra, with the "initialization keys" being used to define the initial key generator settings, and to provide morphing back to the equation.
While STU-III audio quality could be better, conversations can take place at a distance over an insecure phone system that would otherwise require a face to face meeting. While the quality can be improved by using a purely digital STE, the communications infrastructure is rarely able to support their widespread usage.
If you are interested in purchasing any of the equipment listed on this page then please contact us. Granite Island Group offers a full line of communications and technical security products ranging from inexpensive body worn bug detectors and encryption equipment, to full TSCM deployment kits suitable for high threat corporate and diplomatic TSCM inspections.
Our prices and terms are very competitive, and we offer only the highest quality equipment available in the industry (no Spy Shop toys).
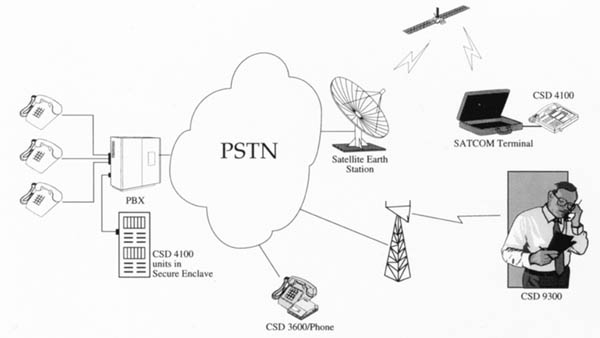

The STU-III telephone was developed to protect sensitive and classified information by way of a secure means easily accessible to a wide variety of users. While most individual conversations are unclassified in themselves, sensitive information can be gathered through analysis of daily routine voice communications. Examples of sensitive information that require protection are logistics, new systems acquisition, contract information, executive movements, and private information concerning personnel matters.
The CSD 4100 is a full featured and highly secure telephone for government applications. It operates in full and half duplex modes, over any public or government switched telephone network, the Inmarsat B and M satellite networks, AMPs cellular networks, as well as radio channels. It is compatible with CSD 3600 secure telephone system.
The CSD 4100 has a variety of security layers for optimum communications protection. A new key is negotiated at each communications session using public key encryption, while private key system adds message authentication and certification. Complete security is confirmed when the receiving security device is identified and indicates that the intended recipient received the call. An easy to read display also shows if the call is or is not protected.
Key generation, transport, storage and access control are centrally managed via WindowsTM based key management system - the KCA 4000. For optimum security, serial numbers are assigned to each telephone unit and key bank. Only users with a crypto ignition key matching the serial number programmed into the CSD 4100 can operate the secure unit. Additionally, a secure call can only be established if the sending and receiving devices are authorized to communicate.
The CSD 4100 has all the telephone features needed by busy executives. Digital encryption for optimum voice quality, a data interface, and a clear/secure speakerphone are a few notable features. Combines secure voice and secure data in one convenient product. Provides superior voice quality. Protects phone calls, facsimiles, electronic mail and computer communications.
Models 1100 and 2100S (for U.S. Government use only) can control access to your computer or fax machine and can screen out unauthorized phone calls. Both units are Controlled Classified COMSEC items, and must be ordered though your COMSEC Account Manager.
On the other hand the Model 4100P and 4100F are not Controlled Classified COMSEC items and as such they are perfect for government applications where classified information is not being protected, but a high level of privacy is still required. Model 4100P is available for US business applications, with the Model 4100F for International use.
The 4100F is ideal for security on international satellite calls such as Inmarsat, M-Sat, Iridium, GlobalStar, and so on. An optional cellular briefcase for remote operation is also available.
The 4100 is the classic government STUIII design (suitable for "sensitive but unclassified" information), which we can normally ship right from stock. This product is the ideal solution for most corporate and government requirements.
Secure operation via CIK (Crypto-Ignition Key) 2.4 HDX and FDX secure voice 4.8 CELP and HDLPC FDX secure voice Clear voice Secure Access Control System (SACS) Display window for authentication identification Automatic self-testing FCC and VDE approved UL and CSA approved MIL-STDs 461C and 454J Optional carrying case Dimensions: 8.5" W X 11.0"L X 2.5" H Weight: 7 pounds
The Model 4100, is an inexpensive encryption device that is simple to use and easy to install. Simply plug in the power cord and the telephone jack. This full function unit works at speeds of 2.4, 4.8 and 9.6 kbps and is government-approved for unattended transmission over standard public telephone lines. The unit can be controlled directly or remotely from a PC or computer terminal.

The Model 4100 STU-III Secure Data Device can be employed to protect sensitive data bases or can be used to establish a secure FAX network or electronic mail system. In each instance, the STU-III Secure Data Device, Model 4100, checks the ID of each incoming data call and automatically compares it to a programmed list of authorized users. Unauthorized calls are terminated without compromising information. The STU-III Secure Data Device, Model 4100, also provides the information needed to construct an audit trail for each data call, whether successful or not.
The STU-III Secure Data Device, Model 4100, is interoperable with other Type 2 devices and all Type 1 STU- III terminals.
Normally factory stock and available for immediate shipment.
Technical Specifications
| CRYPTOLOGY | DACE algorithm Bell Laboratories algorithm |
| KEY MANAGEMENT | Negotiated public key Private key Public key with authentication |
| SECURITY FEATURES | Auto-answer, auto secure Anti-tamper and zeroize Visual authentication identification Plain text inhibit Secure access control via CIK |
| EXECUTIVE TELEPHONE FEATURES | Speaker phone On-hook dialing Pulse or tone dialing Last number redial Memory dialing: 32 numbers Programmable pause Dial tone detect Switch hook flash Automatic disconnect Ringer cut-off Handset volume control 2-line by 16 character LCD |
| DATA RATE | Voice/data: Synchronous/asynchronous 2400, 4800, 9600 bps |
| VOICE MODES | Clear Voice Secure Voice: 9.6 Kbps full duplex MRCELP 4.8 Kbps full duplex RCELP 4.8 Kbps full duplex CELP 2.4 Kbps full duplex LPC-10e 2.4 Kbps half duplex LPC-10e |
| INTERFACE | EIA RS-232 data port with 25 pin D-connector RJ-11/RJ-13 telephone jack |
| POWER | External Power Supply: Selectable, 110/220 VAC Input Frequency: 47-63 Hz |
| STANDARDS COMPLIANCE |
|
| ENVIRONMENTAL | Temperature: Operating: -10o C to +40o C Storage: -40o C to +65o C Humidity: Non-condensing 5 to 95% |
| SIZE AND WEIGHT | Width: 9" (22.86 cm) Depth: 11" (27.96 cm) Height: 3.25" (8.26 cm) Weight: 10 lbs (4.53 kg) |
| SECURE CONFERENCING SYSTEM | Secure automated teleconferencing DOS-based system Optional interface to Enclave |
| OTHER OPTIONS |
|
Model 4100P $Please Inquire


The CSD 3600 is a compact security device that is placed between the base telephone and the handset. With a push of a button, the phone call is protected by Bell Labs high grade cryptographic algorithm and public key encryption. The call can be decrypted by a receiving device including, another CSD 3600 or a CSD 4100 secure executive telephone.
The CSD 3600 generates and distributes keys using negotiated public key encryption. With public key technology, manual key loading and maintenance is not necessary, thus enabling immediate communications protection. Every time the secure button is pushed, the CSD 3600 generates a new key. This key is unique to the session and to the two communicating CSD 3600s. To further secure the call, random variables derived from the unique key are displayed. By comparing the variables, the sender and receiver can detect if the public key negotiation is being tampered with or spoofed.

Voice clarity during the encrypted call provides speaker recognition. Superior voice quality is the result of a sophisticated speech encoding algorithm developed especially for the CSD 3600 by Bell Laboratories.
The CSD 3600 is as small as a hand-held calculator and extremely lightweight. It can be easily carried in a briefcase for use at home or while traveling - even internationally. The CSD 3600 connects to the telephone handset and not to the telephone network. As a result, it can be used conveniently, worldwide, without global network approvals.
One-button operation to toggle between secure and non-secure calls. By pressing a button, the user can "go secure" and protect sensitive information shared in the conversation. Small, lightweight and portable. Plug-in modules provide compatibility with phones used at work, at home or on the road. Provides superior voice quality. All PABX features of the existing telephone system will operate as before.
This unit works well for businessmen who travel and need a compact unit they can use on the phone in their hotel room. Great for executive travel. However, for improved audio quality and interoperability the 4100 is preferred.
The STU-III Secure Voice Device, Model 2600/3600, is interoperable with all other Type 2 products, and is also interoperable (at an unclassified level). The unique advantage of the STU-III Secure Voice Device, Model 2600/3600, is that the users can "go secure" without losing the features and functionality of their existing telephone system.

Technical Specifications CSD 3600
| CRYPTOLOGY | Bell Laboratories proprietary algorithm Negotiated public key Security Features: Audible tone for secure communication activation/deactivation |
| VOICE MODES | Clear voice Secure voice - 4.8 Kbps RCELP |
| MODEM FEATURES | Near/far echo cancellation Frequency offset compensation 4.8 Kbps: CCITT V.32 secure; full duplex |
CSD 3600 SECURE TELEPHONE ATTACHMENT
| HANDSET MODULES | Based on phone type |
| INTERFACES | Two handset jacks |
| POWER | Standard 100-240 VAC operation Input frequency: 50/60 Hz Input power dissipation: 3 watts |
| ENVIRONMENTAL | 0o C to +40o C |
| SIZE AND WEIGHT | Width: 11.43 cm (4.5") Height: 3.3 cm (1.3") Depth: 17.73 cm (6.96") Weight: approx. 0.7 kg (1.55 lbs.) |
| STANDARDS COMPLIANCE | UL FCC CSA TUV |
| OPTIONS |
|
Normally factory stock and available for immediate shipment.
Model 3600 $Please Inquire


Adds full-featured security capabilities to your Merlin communications system. Works as a 10-button phone for voice calls - and as a security device for your most sensitive voice calls and data transmissions.
Fully interoperable with secure phones manufactured for the government's STU-III program. Also compatible with Merlin Legend System 25 and System 75 PABXs. Provides superior voice quality. This product is available thought your local COMSEC Account Manager. Only available as a special order item.
Model 1100M Please Inquire

Delivers secure conferencing capability to your desktop. Links up to 16 secure telephones on a single call. Turns your DOS-based 386- or 486-PC into an easy-to-use control center for secure conferencing. Components include special software and PC-based conferencing and bridging boards. Only available as a special order item.
Optional software package allows you to broadcast data and facsimiles.
This is a special order item.
Model 5000 Please Inquire (Four User System)

Turns your secure telephone into a secure video-telephone. Displays sharp, motion images - up to eight frames per second with 256 colors. The secure speaker-phone or an external camera or monitor can open your conversation to others in the room.
Transmits still images from a video camera or scanner as high-resolution graphics. Unique coding and compression techniques eliminate the smearing that's common to many low bandwidth video-conferencing units.
The inputs and outputs on the unit also allow connection of auxiliary monitors, cameras, and video recorders. Perfect for field reports, teleconferences, and similar activities. Only available as a special order item.
Can be ordered with a four-inch or six-inch screen.
VTDU Please Inquire (six-inch screen)
Facsimile Security Devices
Models 3700 and 3710
Convenient way to protect facsimiles and make certain they go only where you want them to go. Electronic keys verify your fax is sent where you intended. Establishes a protected, closed network, and eliminates the problem of transmission to wrong numbers. Can be attached between any Group 3 fax machine and phone jack. For large corporate networks NET KEY makes implementation quite simple.

This is a scrambler that is installed between the telephone line and the fax machine, it allows regular (unsecure) and secure faxes to be received on the same machine. Great for Executive Travel.

Touch-screen display makes the product simple to operate. Electronic mailbox (Model 3710) stores facsimiles until you are ready to retrieve them with your personal PIN number.
Generates an audit trail of all facsimiles sent and received.
Normally factory stock and available for immediate shipment.
The CSD 3700 enables highly secure and automatic transmission of fax messages. Once received the messages can be stored securely in optional non-volatile memory until the authorized recipient enters their PIN code. Compact and easy to use, the CSD 3700 operates with any Group 3 fax machine.
Under public key exchange, a new random key is produced with each fax transmission. This session key is unique to the two communicating parties. No other unit can generate this key.
The CSD 3700 supports both 'Open' and 'Closed' fax networks. Open networks allow any two people with the CSD 3700 system to send secure faxes. No previous keying relationship is required. Open networks are ideal for industrial use, where an ever-changing number of companies need to communicate with each other.
Closed networks support government and other high security applications, where only specified people are allowed to send and receive sensitive information. The CSD 3700 adds a network (private) key to the public key exchange to form a closed network. Only machines with the same network key can communicate, and each unit can store up to 20 network keys.
The CSD 3700 is easily configured to meet each organization's preferences via a touch-screen display. A password is required for administrator entry and all configuration settings are protected by this password. A wide variety of send and receive configuration options are available.
Sending a secure fax with the CSD 3700 is as easy as sending an unprotected one. In fact, the CSD 3700 can send faxes without being touched. It operates automatically and in realtime, avoiding the need for operator training and intervention. The CSD 3700 is also compatible with all Group 3 fax machines. It simply attaches between the fax machine and the wall telephone jack. Once the power supply is connected and the administrator sets basic configuration options, secure faxing is possible.
The CSD 3710 has all the security, power, and automation of the CSD 3700, but with another level of protection - a Secure Electronic Mailbox. The electronic mailbox provides internal security by eliminating the danger of unattended, confidential fax messages in the fax output tray.
The sender or receiver of an encrypted fax message can direct the fax to be stored in encrypted form in the receiving unit's mailbox. Stored messages are released (deciphered and printed) only after the entry of a valid Personal Identification Number (PIN).
The CSD 3710 supports up to 50 mailboxes and 120 pages of text. A high-capacity memory upgrade is also available. Mailbox memory is protected and retained in the event of power outages.
Technical Specifications
| CRYPTOLOGY | Bell Laboratories' proprietary algorithm |
| KEY MANAGEMENT | Diffie-Hellman negotiated key Network key for closed networks Paired key All key lengths: 192 bits |
| SECURITY FEATURES | Anti-spoofing number Password protected configuration Secure/clear icon banner Tamper resistant design CSD 3710 only: |
| COMPATIBILITY | CCITT G3 fax machines T.30, T4 V.29 transmission at 9.6/7.2 Kbps, V.27 transmission at 4.8/2.4 Kbps, V.21 signaling at 300 bps RJ-11 modular connectors |
| PHYSICAL CHARACTERISTICS | LCD: 40 characters x 25 lines 3.9 in. x 6.3 in. (9.9 cm x 16cm) Dimensions: Weight: |
| ENVIRONMENT | Operating Temperature: +4o C to +37o C (40o F to 100o F) Storage
Temperature: Relative Humidity: |
| POWER | Standard 90-253 VAC operation UL/TUV/CSA approved power supply Input frequency: 50-60 Hz Input power dissipation: 15 watts |
| STANDARDS COMPLIANCE | UL 1459 (phone safety standard) FCC, Part 15, Class B |
| ADDITIONAL FEATURES | Transaction reports Audit trail Journal report Full self-test on power up |
| CSD 3710 MEMORY | 120 pages, 50 mailboxes Non-volatile memory |
| OPTIONS | Mailbox memory upgrades: 360 pages, 720 pages |
Model 3700 Please Inquire (No Internal Storage or Mailboxes) Model 3710 Please Inquire (Internal Storage and Mailboxes)
Cellular briefcase housing adds portability to our desktop Voice/Data Telephones. Rugged housing features shielded design and special mounting to resist damage during transport and use in the field. One product offers cellular capability for both secure voice and data. Gives you wireless operation for facsimiles, electronic mail and computer communications.
This has been replaced by the CSD 9300 (see below).
Model TC3100 Please See Below

Transportable Secure Cellular Telephone Model 9300
Convenient and reliable way to protect your most sensitive cellular calls. Uses state-of-the-art encryption technology. An audible tone and easy-to-read display let you know your call is protected. Offers superior voice quality. Optional handset modules allow you to use the security features of the 9300 with phones you use at the office, at home or wherever you travel.
This is a standard cellular telephone, and a Series 3600 scrambler in one case. The 9300 is very handy for use in a auto, plane or boat. Note the cautions concerning cellular or radio usage and crypto given further down on this page.
Model 9300 $ Please Inquire
Provides simple and cost-effective way to protect classified government data transmissions including facsimiles, electronic mail and computer communications. Transmits information over any public or government switched network at speeds up to 14.4 kbps.
Security Access Control feature allows you to establish a secure, closed network and control access to facsimile machines or data stored on a PC or host computer. Unauthorized attempts are disconnected before the caller has access. Can be operated remotely from any fax, PC or computer terminal connected to its RS-232 data port.
This has been replaced by the CSD 4100 (see CSD 4100 Description).
Model 1910 Please See CSD 4100

Communications Security Device 3324SE
Comprehensive office communications security system that provides voice, fax, and data encryption in a single executive telephone package. Internal storage of 400 ciphering keys, with automatic key exchanges.
The CSD 3324SE is a comprehensive office communications security system that provides voice, fax and data encryption in a telephone package. The CSD 3324SE has a fallback mode which was originally developed for poor HF channels. As a result, secure communications is always possible with the CSD 3324SE, even over the poorest line conditions. The high level encryption and automated key management system protects the most sensitive information. Internal storage of 400 keys coupled with automatic key changes provide complete hands-off security.
Superior voice quality is achieved by two integrated vocoders. The CSD 3324SE actually reduces noise and hiss in poor quality phone lines. Fax encryption is interfaced at the two-wire phone line to allow Group 3 fax encryption regardless of what brand of fax is used. A voice and fax call can even be conducted over the same line connection.
The Model 3324e was recently update to become the Model 3324se which provided longer keys, more key storage, and enhanced audio quality.

The Model 3324SE can be easily configured into a briefcase, provides superior sound quality over a regular STU-III, and provides compatibility with the DSP-9000 tactical radio ciphering system.

Technical Specifications
| ENCRYPTION ALGORITHM | Proprietary TeltectTM non-linear key generator |
| CRYPTO KEY VARIABLES | System key: 1.16 x 1077 Network key: 1.84 x 1019 Local key: 1.84 x 1019 Total keys: 3.93 x 10115 |
| KEY STORAGE | 400 Local keys stored in two keybanks containing 200 keys |
| KEY LOADING | SmartModuleTM keyfill device or keypad entry |
| VOCODERS | 9600 bps Multi-Pulse 4800 bps CELP |
| DATA MODEMS | CCITT V.32: 9600 to 4800 bps CCITT V.22: 2400 to 600 bps |
| FAX MODEMS | CCITT V.29 CCITT V.27/ter |
| TELEPHONE INTERFACE | 2-Wire, RJ-11C connector |
| FAX INTERFACE | 2-wire, RJ-11C connector |
| DATA INTERFACE | 25-pin EIA-RS-232D |
| OPERATING MODES | Autosense voice/fax Autosense voice/data Fax only |
| SIZE AND WEIGHT | 12" by 10" by 2" (30 cm x 25 cm by 5 cm) 9 lbs (4.1 kg) |
| ENVIRONMENTAL | Operating Temperature: 0o C to 50o C Relative Humidity: 10% to 90% |
| POWER | 115 VAC, 60 Hz or 230 VAC, 50 Hz or 10-30 VDC |
| POWER CONSUMPTION | Maximum 7 watts |
| OPTIONS AND ACCESSORIES | SmartModule keyfill device 115/230 VAC switchable power Portable briefcase model |
Model 3324SE $ Please Inquire

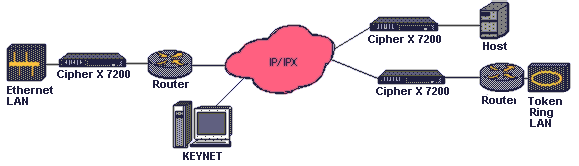
The Cipher X 7200 Internet Protocol (IP) Encryptor (with Ethernet Interface) provides transparent network encryption at data rates up to 10 Mbps. Security at the virtually ubiquitous IP layer allows the Cipher X 7200 to secure most LAN and WAN networks including hybrid networks. The Cipher X 7200 is easily managed with KEYNET, TCC's secure network management application.
The Cipher X 7050 is a versatile digital link bulk encryptor offered in a variety of versions supporting CEPT at 2.048 Mbps, T1 at 1.544 Mbps, RS-232 at 19.200 bps and up to 9600 bps in isochronous mode in full duplex, half duplex or simplex mode.
Protocol sensitive intelligence enables the Cipher X 7200 to provide complete end-to-end and transparent network security. The Cipher X 7200 accepts IP packets from a router or LAN and separates the header information, including addressing and the network management data (i.e. ICMP, RIP, ARP), from the user data. The Cipher X 7200 then encrypts only the user data and leaves the header information in the clear. After reconstruction, the packet is sent securely and transparently over the WAN. No network modification is required. The packet appears the same as any other non-encrypted packet processed by network routers and switches. Higher layer protocols, i.e., TCP, UDP, FTP, and Telnet are also transparent to the Cipher X 7200.
The Cipher X 7200 provides multiple levels of network access protection to ensure that only authorized messages are permitted to transit to and from customer premises. Each virtual circuit is identified by the CipherX by its source and destination address or subnet address, and can be designated as plain, cipher, or blocked. All packets sent to an address designated as cipher have a crypto authentication code at the beginning of the user data field. If this code is missing or incorrect, the packet is rejected, thereby forming a firewall between the WAN and the router on the customer site.
Additionally, a network protected by Cipher X 7200s can be segmented into several discretionary access groups. Individual IP addresses and subnets can be assigned as members of one or more groups, thus affording the system manager complete control over which nodes may communicate.
The Cipher X 7200 is designed to support high traffic IP users. Complex security operations are done efficiently and at high speeds to achieve a maximum data rate of 10 Mbps. Each Cipher X system can secure up to 1,024 simultaneous virtual IP circuits. Each virtual circuit, identified by the source and destination IP address, is protected independently with its own key. A Cipher X under full load is equivalent to 1,024 separate encryption units.
| APPLICATION | WAN security for IP Protocols
Encryption, authentication, and firewall |
| CRYPTOGRAPHY | ANSI X9.52 Triple-DES algorithm
|
| KEY MANAGEMENT | Triple-DES Algorithm
|
| OPERATION | Synchronous, full-duplex |
| DATA RATES | 9.6 Kbps to 10 Mbps full-duplex |
| VIRTUAL CIRCUITS | Up to 1,024 simultaneous virtual IP circuits
Each IP or subnet address designated as Plain, Cipher, or Blocked A unique, random encryption key protects each circuit. |
| PACKET SIZE | To 4,096 bytes |
| MANAGEMENT PROTOCOL SUPPORT | RIP, ARP, ICMP, SNMP |
| STANDARDS | RFC 791, RFC 768, RFC 792, RFC 894 |
| SECURITY STANDARDS | FIPS 140-1, ANSI X9.52, ANSI X9.9, FIPS 171, FIPS 46-2 |
| USER INTERFACE | TCC's Cipher Site Manager application running on Windows PC.
PC connects to Cipher X 7200 via serial asynchronous cable |
| NETWORK INTERFACES | Ethernet AUI or 10 base T |
| SYNCHRONIZATION | Automatic crypto sync recovery upon errored or dropped packet
Error & spoof protected: Secure authentication prevents modification or playback attack |
| AUDIT LOGS | Battery-backed logs for alarms, errors, & security events
Each entry is Time and Date Stamped. |
| EMI/EMC | FCC Part 15, Subpart B, Class B
EN55022 89/336/EEC EN55082-1 1992, Generic Immunity IEC 801-2, ESD Susceptibility IEC801-3, Radiated Susceptibility-Electric Field IEC 801-4, Conducted Transients Susceptibility |
| SAFETY | ANSI/UL 1950
CSA C22.2 No. 950-M89 EN60950 IEC 950 |
| MBTF | Exceeds 30,000 hours @ +25o C ground benign |
| POWER REQUIREMENTS | AC Supply:
Auto ranging: 85-265 VAC 50/60 Hz 20 Watts typical |
| TEMPERATURE AND HUMIDITY | Temperature and Humidity:
0o C to +50o C Operating -40o C to +80o C Storage Up to 90% Humidity, non-condensing |
| SIZE AND WEIGHT | Height: 1.75" (4.4 cm) 1U rack height
Width: 16.5" (41.9 cm) without 19" rack mount ears Depth: 10.5" (26.7 cm) Weight: 15 lb (6.8 kg) |
| OPTIONS AND ACCESSORIES |
|
Cipher X 7200, Internet Protocol (IP) Encryptor
with Ethernet Interface $ Please Inquire

A versatile network security solution for low and medium data rates. Supports X.25 networks, leased lines, and other point-to-point communications. Available in both synchronous and asynchchronous models and protocol sensitive models.The Cipher X 850 provides comprehensive data encryption solutions for either dedicated, point-to-point synchronous data links (Cipher X 850H-PT) or X.25 packet data networks (Cipher X 850H-PS) at data rates up to 64 Kbps. The Cipher X 850 uses a proprietary algorithm for international applications. Acting as a security overlay, the Cipher X units require no network modifications. Each Cipher X 850 unit supports 254 virtual circuits, each secured by a unique key.
| CRYPTOLOGY | Cipher X 850: Synchronous: HyperCrypt TM Asynchronous: TEAL TM |
| KEY MANAGEMENT | Key Management: ANSI X9, Two and three layer Key Diversity: 128 bit Local Key, 8192 bit System key Key Storage: 800 Local Keys, 24 Key Encryption Keys |
| DATA RATE | Up to 64 Kbps |
| INTERFACE OPTIONS | RS-232, RS-422, RS-530 or V.35 |
| POWER | Requirements: 95-260 VAC @ 40-66Hz Power Consumption: Less than 15 watts |
| ENVIRONMENTAL | Temperature: Operating: 0o C to 50o C Storage: -20o C to 80o C EMI/EMC: FCC CFR Part 15, Class B |
| SIZE AND WEIGHT | 3 x 9.5 x 14.4 inches 7.6 x 24 x 36 cm 11 lbs/5kg |
| DIAGNOSTICS | Manual and automatic self tests Error and alarm logs Remote monitoring from KEYNETTM |
| MODEL OPTIONS | Cipher X 850 PS X.25: X.25 protocol sensitive, data rates up to 64 Kbps, 254
simultaneous virtual circuits, KEYNET compatible. Cipher X 850 PT Sync: Synchronous protocol transparent, data rates up to 64 Kbps, full and half duplex. Cipher X 850 PT Async: Asynchronous protocol transparent, data rates up to 9.6 Kbps, simplex, half and full duplex |
| KEYNET SYSTEM: | On-line key management On-line diagnostics and polling Hot standby capability Unix workstation system SNMP proprietary MIB |
| CRYPTO MANAGEMENT SYSTEM (CMS): | Off-line key management Random key generation Key loading and archive PC-based system |
| ACCESSORIES: | SmartModuleTM key and configuration fill device KFD-800 keyfill device 19" rack mount Spares packages Training Extended warranty/next day replacement |
CIPHER X 850/PT Network Security Encryption Device (Protocol Transport Link Encryptor, Synchronous up to 64 kbps) $ Please Inquire CIPHER X 850/PS Network Security Encryption Device (Protocol Sensitive Network Encryptor, X.25, 64 kbps) $ Please Inquire

Strategic security for high data rate signals in demanding environments. Critical applications such as missile firing commands, emergency military telephone networks, and command and control networks.
The DSD72A-SP Encryption System provides strategic security for high data rate signals in demanding environments. Critical applications such as missile firing commands, emergency military telephone networks, and command and control networks are protected today by the DSD72A-SP.
Maximum cryptologic security for military and top-level government applications is achieved with as SNARK TM key generator and automated key management. Two crypto synchronization methods, long cycle and cipher feedback, are built into the system and allow it to stay on-line in a variety of error and jamming environments.
Automated and secure key management throughout the key life cycle is provided by the DSD72A-SP and Crypto Management System (CMS). The DSD72A-SP stores 800 keys, a much greater number than any other system, to minimize the need to load new keys.
Truly random keys are generated and allocated by the CMS. SmartModuleTM and KFD 800C, two high capacity and secure key transport devices, are used to deliver and load keys into the encryption units. The keys are encrypted for distribution, so a loss of a key transport device does not jeopardize the security of the network.
Once the full set of 800 keys are loaded into the unit, key management is automatic. Keys can be automatically changed on a timed basis. Even with daily changing keys, new keys need only be loaded once every two years. Downline indexing keeps a communicating pair of DSD72A-SP units on the same key. No sensitive keying information is sent over the air, only the key index numbers are sent.
All keys are stored in a battery backed RAM capable of retaining the keys for five years without power. Tamper resistant packaging causes keys to be erased if a unit is opened. Keys may also be destroyed quickly and simply from the front panel to protect their secrecy in case of imminent overrun.
Remote control of encryption minimizes the need to send field service to the unit for ordinary diagnostics, configuration or preventive maintenance. This information is accessible remotely in both centralized and decentralized networks.
In centralized networks, a CCMS with Command Link TM connection to each DSD72A-SP can do most everything that can be done at the front panel of each unit in the network. Diagnostics, access to error and alarm logs, configuration, key allocation and usage and other functions are available and programmable at the CMS system.
In decentralized networks, on the other hand, DSD72A-SP units form communicating pairs with each pair having a designated Master unit. The Master unit is placed at the more accessible site and has the ability to check remote unit status, run remote diagnostics and access error and alarm codes.
Applications
Technical Specifications
| CRYPTOLOGY | Key Generators: SNARKTM PK2M or MKG non-linear key generators Modes of Operation: |
| KEY MANAGEMENT (SNARKTM) |
Crypto Key Variables: 120-bit Local Key 8-bit Network Key 128-bit MKEK (Optional) Key Storage: Key Loading: |
| DATA RATE | Full Duplex at 64 Kbps to 34 Mbps |
| REMOTE OPERATION | Diagnostics from remote DSD72A-SP CMS centralized control of key management, configuration and diagnostics |
| INTERFACE OPTIONS | CCITT G.703/CEPT E1 CCITT G.703/CEPT E2 North American T1 Eurocom D/1 ATACS TRI-TAC V.35/RS-422 Other interfaces upon request |
| POWER | DC: 24V to 48V nominal, ±20% or AC: 85V to 264V, 47 Hz to 440 Hz Power Consumption: |
| ENVIRONMENTAL Mil Std 810D | Operating Temperature: -20o C to +70o C Storage Temperature: Humidity: Rain: Transit Drop: Shock: Vibration: Altitude: EMI: MTBF: |
| SIZE AND WEIGHT | 35.6 D x 43.2 W x 15.3 H cm 14 L x 17 W x 6 H inches 11.4 kg (25 lbs) |
| DIAGNOSTICS (BITE) | On-line tests: No data, keyfail, CPU, ROM integrity and key table integrity Off-line tests: CPU, RAM, ROM, LED, LCD, keypad, self-loop and Command LinkTM |
| ACCESSORIES |
|

The DSP-9000 is a family of Military Ciphering Systems that provide long-term, stand alone strategic security for communications transmitted over narrowband channels. Available in a base station, manpack, handset, and implantable board configuration. Capable of securing virtually any HF, VHF, UHF, or satellite application.

The DSP-9000 is an extremely versatile system where the handsets can be used with tactical manpacks out in the field, with base unit being used a centrally controlled key distribution point.
The DSP-9000 is fully compatible with the 3324SE system which allows efficient communications between all levels of command.
The DSP 9000 utilizes leading edge technology throughout its design. A powerful Digital Signal Processor supplies tremendous computing power that is used to ensure exceptional recovered voice quality and cryptographic security. All audio input/output parameters are software controlled. This allows a single DSP 9000 to be quickly installed on a variety of radios without modifying the hardware.
Exclusive features such as half and full duplex versions, dual synchronization, automatic voice/data encryption selection and storage of a large number of keys also clearly separate the DSP 9000 from its competitors. Additionally, the DSP 9000 is compatible with CSD 3324SE secure telephone to enable "office-to-field" communication.

HF SSB communications networks presents several unique problems to any kind of encryption system; however, the DSP-9000 is one of the few cipher systems which operate flawlessly with such situations and is ideal tactical HF radio systems.

Features
Secure Applications
Key Management and Cipher Technique
Enhanced Domain Transform encryption technique begins by using a toll quality voice digitizer operating at 64 Kbps. The digitized audio is then pseudorandomly transformed from frequency into time and time into frequency using "Enhanced Domain Transform" technique. This transform combined with a proprietary compression technique eliminates virtually any residual intelligibility.
The domain transform is controlled by a highly non-linear digital key generator. This crypto algorithm can be modified by the customer using Crypto Management System. One of the selected encryption keys stored in the DSP 9000 and a randomly generated Initialization Vector (IV) provide a new keystream for each synchronization.
Completely automatic 'hands off' key management approach is ideal for military applications. All key management parameters can be selected and controlled by a COMSEC security officer, thereby eliminating potential operator errors or compromise. The transmitting unit selects the appropriate key by means of a real time clock at a time interval set by the security officer. Automatic downline key indexing insures that the receiving unit always selects the proper key for decryption.
Handset Model
Advanced DSP technology and the latest miniaturization techniques have allowed the high level security and voice processing of the DSP 9000 base station to be reduced in size to fit in a handset configuration.
It is no longer necessary for field soldiers to carry a separate crypto unit. The DSP 9000 HS replaces the existing radio handset, thereby adding less than one pound to the weight of the manpack radio. Prior to a mission, a security officer loads the DSP 9000 HS with 200 keys and radio interface settings using a SmartModuleTM. Once loaded, the radio operator need only select cipher or plain mode. With the addition of the HS model, the DSP 9000 family now provides a complete, integrated security solution for air, ground and sea operations.
Technical Specifications
| ALL DSP 9000 UNITS: | |
| CIPHERING TECHNIQUE | Proprietary Enhanced Domain Transform (EDT), controlled by a non-linear Key Generator |
| CRYPTO KEY VARIABLES: | System key: 8.39 x 1079 Network key: 6.55 x 104 Local key: 7.2 x 1016 Total keys: 4.0 x 10101 |
| SYNCHRONIZATION | Inband digitally controlled FSK sync burst (74 bits) |
| FREQUENCY CONTROL | High-stability crystal oscillator |
| FREQUENCY OFFSET | +/- 120 Hz maximum for HF-SSB |
| AUDIO INTERFACE | 'Soft' Selectable Interface Characteristics |
| AUDIO BANDWIDTH | Voice Mode: 200 Hz to 2800 Hz Data Mode: 200 Hz to 3000 Hz |
| REQUIRED CHANNEL BANDWIDTH | 500 Hz to 2400 Hz Minimum |
| DIAGNOSTICS | BITE run at power on and on demand from keypad |
| Humidity: 120 hours, 95% non-condensing MIL-STD-810C, Method 507 | |
| EMI | MIL-STD-461B, Class A3 |
| MTBF | Exceeds 10,000 hours per MIL-HDBK-217F & MIL-STD-756 |
| OPTIONS AND ACCESSORIES | Crypto Management System SmartModuleTM keyfill device |
| DSP 9000 BASE STATION | |
| KEY MANAGEMENT | |
| Key Storage: 800 Local Keys stored in two keybanks containing 400 keys | |
| Key Loading: SmartModuleTM or KFD-800 keyfill devices, or keypad entry | |
| OPERATION: | Half duplex and Full duplex models |
| SIZE AND WEIGHT | Height: 2.25" (5.7 cm) Width: 8.25 " (21 cm) Depth: 11.0" (28 cm) Weight: 5.7 lbs (2.6kg) half duplex; 6.8 lbs (3.1kg) full duplex |
| POWER | DC Voltage: +9 to +32 VDC AC Voltage: 115/230 VAC, 50/60 Hz Current: 1 watt (90mA@12VDC) |
| AUDIO INTERFACE | H-189/HC-250 handset 4 wire/600 ohm MIC/Speaker Telephone direct wired |
| PUSH TO TALK SIGNAL | Contact closure to ground or to positive supply (+32 V max) |
| DIAGNOSTICS | Full range of BITE including: CPU, RAM, ROM, DSP, analog test, audio loop, keypad, keyfail, key storage and display. |
| ENVIRONMENTAL | |
| Temperature: Operating: -20o C to +70o C Storage: -40o C to +85o C | |
| Vibration: 1.5G peak, 55-220 Hz MIL-STD-810C, Method 514 | |
| Shock: 40Gs @ 11ms MIL-STD-810C, Method 516 | |
| OPTIONS AND ACCESSORIES |
|
| DSP 9000 HANDSET | |
| KEY MANAGEMENT | |
| Key Storage: 200 Local Keys stored in two keybanks containing 100 keys | |
| Key Loading: SmartModuleTM keyfill device, or keypad entry | |
| OPERATION: | Half duplex |
| SIZE AND WEIGHT | Height: 9" (23 cm) Width: 2" (5.1 cm) Depth: 4" (10.2 cm) Weight: 2.0 lbs (.9kg) |
| POWER REQUIREMENTS | Externally supplied, 9 - 18 VDC 1 watt (90 mA @ 12 VDC) |
| AUDIO INTERFACE | 6-pin MIL-C-55116 connector Aux connectors with DC power Others available on request |
| PUSH TO TALK SIGNAL | Contact closure to ground |
| ENVIRONMENTAL | |
| Temperature: Operating: -20o C to +60o C Storage: - 40o C to +85o C | |
| Waterproof: Submersible to 1 meter | |
| Vibration: 1 Grms, 5-200 Hz random curve MIL-STD-810D, Method 514.3 | |
| Shock: 100 G's at 11 ms MIL-STD-810D, Method 516.3 |

High Security Scrambler used for military tactical uplinks and downlinks

Full Satellite system in briefcase for military tactical uplinks and downlinks

French made tactical scrambler made by Thompson-CSF, very popular with NATO troops. Frequently used on walkie-talkies, and vehicle radios.


Racal Audio Scramblers
Various encryption devices made by Racal, both are available with DES. The module on the right can be fitted to most Racal tactical radios.

Datotek is a widely used, low cost builder of encryption systems used worldwide
The KG-84A/C is cryptographic equipment developed to ensure secure transmission of digital data. The KG-84C is a Dedicated Loop Encryption Device (DLED), and both the KG-84A/C are General-Purpose Telegraph Encryption Equipment (GPTEE). The KG-84A is primarily used for point-to-point encrypted communications via landline, microwave, and satellite systems. The KG-84C is an outgrowth of the Navy high frequency (HF) communications program and supports these needs.
The KG-84A and KG-84C are devices that operate in simplex, half-duplex, or full-duplex modes. The KG-84C contains all of the KG-84 and KG-84A modes, and a variable update counter, improved HF performance, synchronous out-of-sync detection, asynchronous cipher text, plain text, bypass, and European TELEX protocol. The KG-84 (A/C) is certified to handle data at all levels of security. The KG-84 (A/C) is a Controlled Cryptographic Item and is UNCLASSIFIED when unkeyed. Keyed KG-84 equipment assumes the classification level equal to that of the keying material used. Capable of data rates up to 64 kbps synchronous and 96 Mbps asynchronous.
The KIV-7 family of embeddable KG-84 communications security (COMSEC) modules are lightweight, compact, commercial off-the-shelf (COTS) cryptographic devices that provide protection for digital and voice communications. The KIV-7 provides security protection through TOP SECRET, dependent on the classification of the fill key. There are currently three models in the KIV-7 family: the normal speed (KIV-7), the high-speed (KIV-7HS), and the high-speed revision A (KIV-7HSA). The KIV-7 cryptographic device was designed as a miniaturized KG-84A/C and intended to be completely interoperable with KG-84A/Cs, however, the KIV-7 and the KIV-7HS contain the Windster processor chip, which has some performance anomalies that prevent total KG-84A/C interoperability.
The KIV-7HSA with the Presidio processor chip is being evaluated to ensure it resolves the Windster chip anomalies and is scheduled to be available in FY99. Only the high-speed version (KIV-7HS) is now being manufactured. The miniaturization of the KIV-7 family units makes them suitable for space and load constrained environments (e.g., aboard submarines or vehicle mount).
The KIV-7 has storage for up to 10 traffic encryption keys, which simplifies multinet communications. A removable cryptographic ignition key (CIK) prevents unauthorized access and protects all internally stored keys. The KIV-7 fill interface is compatible with both DS-101 (AN/CYZ-10 Data Transfer Device [DTD]) and DS-102 (KYK-13, KYX-15, KOI-18) common fill devices. When unkeyed or when the CIK is removed; and not collocated, the KIV-7 is handled as an UNCLASSIFIED controlled cryptographic item (CCI). When the KIV-7 is keyed, it is handled at the classification level of the highest level of stored key.
The KIV-7 Rack Assembly provides both electrical and mechanical interfaces to accommodate 2, 4, or 8 KIV-7 units. The 19-inch rack assembly is designed for installation into any standard 19-inch cabinet that meets the design requirements of RS-410. The assembly contains two interchangeable power supplies and an automatic switchover circuit.
The WALBURN Family (KG-81, KG-94/194, KG-94A/194A, KG-95-1,2, and R) equipment consists of high-speed bulk encryption devices used primarily for encryption of microwave trunks, high-speed landline circuits, video teleconferencing, and T-1 satellite channels.
WALBURN Family devices are certified to encrypt and decrypt up to TOP SECRET. They are UNCLASSIFIED controlled cryptographic items (CCIs) when unkeyed. These devices provide full-duplex/simplex encryption for all classification levels and are cryptographically compatible and interoperable (within their respective data rates).
KG-81: Provides full-duplex encryption of digital trunks. It is rack mounted using the HNF-81-1/2 interconnect housing frame. The KG-81 is used primarily at major communications stations for bulk data and video encryption.
KG-94: Provides emerging low and medium tactical and nontactical digital trunk encryption. It is rack mounted using the HNF-81-1/2 interconnect housing frame and supports the Joint Tactical Communications program in association with Marine Corps AN/TTC-42 and AN/TRC-170 switches.
KG-94A: Is an environmentally repackaged, ruggedized version of the KG-94 that supports the Marine Corps unit level circuit switches (SB-3865) and the Digital Wideband Transmission System(DWTS).
KG-194: Is a less costly version of the KG-94 that incorporates a remote keying capability and implements FIREFLY technology. The KG-194 is used for digital and voice bulk encryption at major communications stations.
KG-194A: Is a less costly ruggedized version of the KG-194. It satisfies the same basic requirements as the KG-94A, incorporates a remote keying capability, and implements FIREFLY technology.
KG-95: Is a general-purpose, high-speed, full-duplex, fixed-plant, key-generating encryption device used for video, data links, missile test range communications (KG-95-1), and DS-3 (45 Mbps) telephone trunks (KG-95-2). Its capabilities include remote operation, remote status check, and remote over-the-air rekey exchange, in addition to new key management techniques and a fiber optics interface. The KG-95R is a composite of two KG-95-2s in a redundant configuration.
KIV-19: Is a miniaturized KG-194 that is functionally equivalent and interoperable with the KG-194 and KG-194A. The KIV-19 is not intended to replace the KG-194 and KG-194A but to fill new requirements and unique backfit requirements that have strict size and weight constraints. The KIV-19 is certified to secure all classification levels and categories. It is an UNCLASSIFIED controlled cryptographic item (CCI) when unkeyed. When keyed, the equipment carries a classification equal to that of the key installed.
HNF-81-1: Is approved for all levels of classified traffic and is designed to have one or two KG-81, KG-94, or KG-194 cryptographic devices. The terminal blocks in the rear of the HNF-81-1 provide connections between the input or output cabling and the connectors.
HNF-81-2: Is approved only for the transmission of unclassified or previously encrypted traffic unless it is transmitting bypassed information with prior approval of National Security Agency(NSA). The HNF-81-2 is mechanically similar to the HNF-81-1 except the terminal blocks in the rear of the frame are mounted on printed wiring boards giving the user cryptographic bypass ability.
The HAYFIELD MCM is a programmable four-channel receive-only device developed for receivers used to decrypt the Tactical Receive Equipment and Related Applications (TRAP) Data Dissemination System (TDDS) broadcast. It incorporates DS-102 and DS-101 key loading and is Electronic Key Management System (EKMS) compatible. It has internal storage for six algorithms and 64 keys and is capable of performing over-the-air rekey (OTAR). The HAYFIELD MCM is packaged in a 160-pin quad flat pack.
The initial application is for the KGR-96 function only, but other algorithms are being developed in software for incorporation into HAYFIELD. These include the KGV-11 function, the KG-84 function for secondary imagery reception, and the KG-40A function (High Speed Fleet Broadcast).
The HAYFIELD MCM is certified to decrypt traffic TOP SECRET/SI and below. The HAYFIELD is an UNCLASSIFIED controlled cryptographic item (CCI) when unkeyed. When keyed, it carries the classification level of the traffic key loaded into the host equipment.
The RAILMAN is a low-speed full/half-duplex embeddable standard communication security (COMSEC) module used to secure digital voice or low speed data traffic. It consists of a custom CMOS Large Scale Integrated Circuit (LSIC) in a 121-Pin Grid Array (PGA) package supported by an off-the-shelf SOS RAM. The module provides security for classified traffic up to 500 Kbps.
The RAILMAN is approved for processing classified information through TOP SECRET level. It is an UNCLASSIFIED controlled cryptographic item (CCI) when unkeyed. When keyed, it carries the same classification as the key that is loaded. The RAILMAN was designed to be embedded into various voice/data equipments, such as mobile telephones, modems or manpack radios.
RAILMAN provides cryptographically interoperable traffic/rekey operation with KY-57/58, E-DRZ, KYV-2, KYV-5, KG-84, KIV-14, KY-99A, KY-100, WINDSTER, and STU-III. The RAILMAN is presently being embedded into the SINCGARS II radio, AIRTERM/MINTERM radio and the Unit Level Circuit Switch (ULCS).
Click here for a Sample STU Policy Concerning the Use of a STU in a Private Residence in PDF Format.
Click here for a STU-III Voice and Data Terminal, SCS Models 1100/1150 User's Manual in Word Format.
Click here for the Department of Defense Security Institute STU-III Handbook for Industry.
|
"Gentlemen do not read each other's mail" - Secretary of State Henry L. Simpson, August 1929, Shutdown and dismantled the "American Black Chamber"
"Henry Simpson is a naive fool"
"Not only do gentlemen read each other's mail, but wise gentlemen study and practice it as an art form."
|
CipherTalk 8000 Hardened
Secure GSM International Telephone
[CT-8000 Brochure]
Communications monitors can identify STU-III lines, so these phone numbers are obvious targets. Therefore, a STU-III line being used in non-secure mode may be more likely to be monitored than another line that never carries encrypted communications. Maintaining strict telephone security discipline is critical.
Questions sometimes arise concerning how to transport the STU-III on commercial flights. On commercial airlines, a courier letter is usually required for transport of a STU-III, even if unkeyed (either no key loaded, or CIK is removed). The STU-III MUST be carry-on luggage (cannot be checked), and must remain within immediate sight and control of a cleared person at all times. If you go to the bathroom during the flight, it goes with you, unless you are traveling with another cleared person who can watch it while you are away from your seat. Given the sensitivity of the key and the STU-III itself, measures should be taken to ensure that the STU-III remains within your control at all times. It is not a problem to allow a STU-III to be physically examined (NOT OPENED), and powered up at airport security checkpoints. It may even be X-rayed without ill effects. This does not apply to the keys which must be carried on your person, can not be X-rayed and may never leave your possession unless in secure storage or in the presence of cleared personnel.
When a STU-III key is inserted into the STU-III, this STU-III becomes classified and must be protected as classified material. This means that only cleared personnel are authorized to use the STU-III. When the STU-III key is removed and properly stored, the remaining STU-III telephone can be treated an unclassified material. Without the keys, a STU-III is just valuable, unclassified government property.
Ensure that all personnel are familiar with the location of the zeroize button (but don't touch it) on the STU-III. Only when required by an Emergency Destruction, such as a possible overrun or seizure, should the rear flap be lifted and the red button pressed. Zeroizing disables the STU-III.
The Secure Telephone Unit Third Generation (STU-III) is the newest communications system that meets the need for protecting vital and sensitive information over a telephone system. The STU-III is a compact, self-contained desktop unit capable of providing the user with clear and secure voice and data transmissions. The unit is fully TEMPEST protected and is certified by the National Security Agency for use up to and including Top Secret material.
The STU-III is unique in that it works as an ordinary telephone and as a secure telephone network to other STU-III terminals. For secure transmissions, the STUIII uses a unique keying system.
The STU-III is operated the same as any telephone. That is, you pick up the handset, wait for a dial tone, then dial the number of the person you want to call. All calls on the STU-III are always initiated in the clear voice mode. Once the party you have called has answered, you have the option of talking to that person in the clear voice mode, clear data mode, secure voice mode, or the secure data mode.
Terminal Setup
The STU-III terminal uses special keys with a designator of KSD-64A. The KSD-64A is a plastic device that resembles an ordinary key. Two types of keys are used with the STU-III, the seed key and the crypto-ignition key (CIK). The seed key is a special keying material used for the initial electronic setup of the terminal. The CIK key is used by the users to activate the secure mode.
When the STU-III terminal is first installed, the COMSEC custodian sets up the terminal with the seed key. A seed key is issued to a particular terminal only. The seed key contains a microchip that is embedded electronically with identification information. This information includes the level of security authorized for that terminal.
Once the COMSEC custodian inserts the seed key into the terminal, the information on the key is transferred to the internal memory of the terminal. At this point, the seed key no longer contains any information and is considered to be "empty."
The information in the terminal is electronically registered with the Key Management Center (KMC). The KMC is the central authority responsible for controlling the key material and issuing reports of compromised keys. The user can discuss classified information up to the security level that has been keyed to the terminal.
The crypto-ignition keys (CIKs) can now be made for users to activate the secure mode. The CIKs are "empty" keys with no information embedded in the metal strip. When the empty keys are inserted into the terminal, some of the information that is now stored in the terminal from the seed key and other information in the memory is transferred onto the metal strips. This information becomes an electronic "password" on the CIKs for that particular terminal, making the CIKs unusable on other terminals. The terminal maintains a list of authorized CIKs for each key in its memory.
Levels of security classification, keying instructions, rekey instruction, CIK management will be decided by the user and the user's communications facility. All users must meet the minimum security clearance requirements.
Secure Mode
As mentioned earlier, the secure mode of the STU-III is activated and deactivated using a CIK. When the CIK is inserted into the terminal, the STU-III can be used in the secure mode up to the classification of the keying material. Without the CIK, the STU-III operates as an ordinary telephone.
Calls are always initiated in the clear. To go from a clear to a secure voice transmission, either caller simply presses his or her SECURE VOICE button after the CIK is used to activate the secure mode.
Once a secure link has been initiated, the two STUIII terminals begin exchanging information. The information exchanged includes the identity of the CIK of the distant-end person, the list of compromised CIKS, and the common level of classified security information to which the two callers have access.
When two terminals communicate in the secure mode, each terminal automatically displays the authentication (identification) information of the distant terminal. This information is scrolled through the display window during secure call setup. The first line of the identification information and the classification are displayed for the duration of the secure call.
The information displayed indicates the approved classification level for the call, but does not authenticate the person using the terminal. Each terminal user is responsible for viewing this information to identify the distant party and the maximum security classification level authorized for the call.
STU-III Administration
The STU-III terminals and keys are COMSEC material. The terminals and keys may be administered either through the COMSEC custodian. Both the terminals and keys are issued to users and must be signed for. Since the seed key is classified, it must be afforded protection for the level of classification in accordance with Secure Telephone Unit Third Generation (STU-III) COMSEC Material Management Policy.
Because CIKs permit the STU-III terminals to be used in the secure mode, the CIKs must be protected against unauthorized access and use. CIKs may be retained by the users who sign for them on local custody. Users must take precautions to prevent unauthorized access and must remember to remove the CIKs from the associated terminals.
When the terminals are unkeyed, they must be provided the same protection as any high-value item, such as a personal computer or laptop. When the terminal is keyed, the terminal assumes the highest classification of the key stored within and must be protected in accordance with the classification of that key.

Establishing a STU secured call from an Inmarsat MES to another STU telephone is exactly as with any normal phone call. Once the call is connected, the STU's secure button is then pressed and the STUs begin exchanging encryption keys to lock the communications.
Both STUs displays will then usually read "Secure" to confirm the privacy of communications. STU is supported by the Inmarsat-B service at rates up to 9.6kbps while Inmarsat-M rates of up to 4.8kbps are possible.
For the very popular mini-M terminals, STU-secured calls are made at 2.4kbps. Special protocols (transparent software) are required in both the mobile and land earth stations to facilitate to the use of STU via Inmarsat.
Many secure telephones used for voice communication also offer RS232 connections for secure data transfer. Encryption equipment with V.26 and below modems, operating asynchronously, have been successfully employed with mini-M, while equipment with v.32 modems are used with Inmarsat-B at up to 9.6.kbps subject to their interfacing requirements. Many link encryption devices already employed in a wide range of terrestrially networked applications have been proven via Inmarsat. These cryptos are used, on-line, in conjunction with Inmarsat-B High-Speed Data (56-64kbit/s) services to ensure the security of critical applications such as video-teleconferencing, high-speed file transfer and store-and-forward video.

Inmarsat - [in PDF Format]
Inmarsat - [in PDF Format]
Inmarsat - GSP1600 Quick Reference Guide [in PDF Format]
Inmarsat - Gigaset 3000 [in PDF Format]
Inmarsat - TA Hookup [in PDF Format]
Inmarsat - Mini M Quick Start [in MS Word Format]
Inmarsat - [in MS Word Format]
Inmarsat - Video Conference Guide M-4 [in MS Word Format]
Inmarsat - Video Surveillance Guide M-4 [in MS Word Format]
Inmarsat - World Communicator Guide [in MS Word Format]
Inmarsat - GStar [in MS Word Format]
Inmarsat - DATA via Worldphone [in MS Word Format]
Inmarsat - G-Star QUICK START-2 [in MS Word Format]
Inmarsat - Encryption on M-4 #1 [in MS Word Format]
Inmarsat - Encryption on M-4 #2 [in MS Word Format]
Inmarsat - Modem Setup [in MS Word Format]
Inmarsat - World Phone Advantages [in MS Word Format]
Inmarsat - Dial-up Networking [in MS Word Format]
Inmarsat - Additional Settings [in MS Word Format]
Inmarsat - WorldPhone Guide [in MS Word Format]
A STU-III secure telephone or "Standard Telephone Unit" is available in five types of encryption strength. Of course the stronger the encryption the greater the difficulty in obtaining the unit, and more restrictive the conditions of sale.
| Type 1 | Restricted to the US Government, Military, and Intelligence agencies Suitable for highly classified information, the customer must have a NSA COMSEC Account to obtain this phone.
|
| Type 2 | Restricted to the US Government and Military Suitable for unclassified information. Tough to obtain due to the paperwork overhead, generally a Type 4 is a better choice.
|
| Type 3 | Restricted to US and Canadian companies and citizens Very difficult to obtain due to the paperwork overhead, generally a Type 4 is a better choice.
|
| Type 4 | Generally available to international companies and citizens, subject to export approval. Suitable for Sensitive But Unclassified or "SBU" information. Perfect for government applications where a high level of privacy or security is needed, but actual classified information is not being passed though the unit. Normally in-stock with fast turn around time.
|
| Type 5 | Fairly unrestricted public key version of above Type 4 equipment, Very Exportable, and available for private sale. Normally in-stock with fast turn around time.
|
A STU-III secure telephone or "Standard Telephone Unit" is only one type of common secure encryption device. A newer STE or "Standard Telephone Equipment" is also in common use, but it does require an special ISDN line or similar digital connection. This presents a provisioning problem as STE's can not be used on ordinary analog lines.
The first-generation Standard Telephone Unit was introduced in the early 1970's, and stores a unique sequence of random bits for encoding, decoding and authenticating information, a function activated by a key-shaped piece of plastic with an embedded computer chip that is inserted into a key loader slot in the telephone. Some lower cost versions of STU-III's are available which do not utilize a removable or changeable key, so ensure the version you are buying has the level of security you are seeking.
A STE (Standard Telephone Equipment) is built for and works best in an all-digital environment; usually an ISDN line whereas a STU-III is an analog device designed for normal analog telephone circuits. When STU-III rings, callers insert their key devices, push a button and wait 15 to 20 seconds for the two phones to exchange encryption codes. The delay "is a nuisance" and can be even longer if one caller is in a country with a less sophisticated telecommunications infrastructure.
STE, however, is automatically secure if both callers are using STE systems and the phones exchange codes in the time it takes to pick up the ringing telephone.
The real advantage is that in that in a secure environment, there's substantial improvement in voice quality, and the time to go secure is almost invisible to the customer and goes automatically secure in that brief instance, and you have to do something to make it unsecure. On the other hand a STU-III goes unsecure, and you have to do something to make it secure.
The trade-off is that a STU-III is fairly low cost, and will work on virtually any telephone system, circuit, satellite connection (such as Inmarsat), or any kind of normal loop line connection. A STE is expensive and needs special (hard to obtain) digital circuits.
The Secure Terminal Equipment (STE) is the evolutionary successor to the STU-III. The STE program improved secure voice communications by changing out the analog STU-III products with digital-based STE products. The STE cryptographic engine is on a removable Fortezza Plus KRYPTON Personal Computer Memory Card International Association (PCMCIA) Card, which is provided separately. The STE Data Terminal provides a reliable, secure, high rate digital data modem for applications where only data transfer (FAX, PC files, Video Teleconferencing, etc.) is required. All STE products will be STU-III secure mode compatible with the following enhanced capabilities:
Voice-recognition quality secure voice communication.
High-speed secure data transfers (up to 38.4 Kbps for asynchronous or 128Kbps for synchronous).
A tactical version, STE/Tactical is a replacement for MMT 1500 with a Digital Non-secure Voice Terminal (DNVT) adapter. Though not a direct replacement for the KY-68, the STE/Tactical can serve as a DNVT replacement with secure voice communication capabilities in STU-III modes over TRI-TAC/Mobile Subscriber Equipment (MSE). STE/Tactical is not secure mode compatible with the Digital Secure Voice Terminal DSVT KY-68.
A STE Direct Dial capability, comprised of the STE/C2 Tactical terminal and/or associated STE/Interworking Function(s) will improve on the existing Navy "Direct Dial" secure voice ship to shore dial-up operations. STE Direct Dial improves secure mode connectivity, provides operational flexibility support for both plain text and cipher text voice modes, and provides a standardized secure ship digital telephone system solution and Joint CINC interoperability with forces at sea and ashore.
Individual STE Product Capabilities:
STE/Office provides enhanced STE capabilities over digital ISDN and STU-III over analog PSTN.
STE/Data provides STE and STU-III data capabilities only.
STE/Tactical with Wedge supports STU-III Black Digital Interface (BDI) over TRI-TAC/MSE or RF asset.
STE Direct Dial
STE/C2 Tactical with Wedge supports STU-III BDI over ISDN or RF asset.
STE/IWF provides interface with PSTN (Analog) and ISDN (Digital).
Certification of STE will provide security for all levels of traffic, up to and including TOP SECRET Special Compartmented Information (TS-SCI). When a Fortezza Plus KRYPTON Card is inserted into a STE, secure storage must be provided to the extent required by Operational Navy Instruction (OPNAVINST) 5510.1 (series) for the maximum classification level of the key used. Fortezza Plus KRYPTON Card is considered classified to the maximum level of key classification until it is associated with a STE terminal. Once associated with a STE terminal, the card is considered unclassified when not inserted in the associated STE terminal.
A STU-III is a highly sophisticated digital device; however, they suffer from a particular nasty vulnerability to strong RF signals that if not properly addressed can cause the accidental disclosure of classified information, and recovery of the keys by an eavesdropper. While the unit itself is well shielded, the power line feeding the unit may not have a clean ground (thus negating the shielding).
If the encryption equipment is located within six to ten wavelengths of a radio transmitter (such as a cellular telephone, beeper, or two way radio) the RF signal can mix with the signals inside the STU and carry information to an eavesdropper. This six to ten wavelengths is referred to as the "near field" or the wave front where the magnetic field of the signal is stronger then the electrical field.
As a rule all COMSEC equipment should be kept out the "near field" by a factor of at least 2.5 to 3 times to get it outside of the field transition point. Simply put, there needs to be a "danger zone" or exclusion zone around any and all COMSEC gear 2.5 to 3 times the near field distance, or 16 to 30 times the longest signal wavelength (the lower the frequency the longer the wavelength).
A "wavelength" is inversely proportional to frequency being used which means that an 800 MHz cellular phone (near a STU) presents a greater direct threat that a higher frequency PCS phone operating in the 1.7 GHz region. On the other hand a PCS or CDMA telephone creates a greater spectral density and far more transitions which allows an eavesdropper to corelate on the signal with more precision.
We also have to consider the amplitude of the signals as well as the "danger zone" created by the transition point or radius of the near field (times 2.5 to 3). When any RF signals inside the "danger zone" exceed -50 dBm (or -77 dBm in some cases) there is still a problem even though the cryptographic equipment is some distance from the actual transmitter, cellular phone, pager, etc. These relatively high signal levels (above -50 dBm or -77 dBm) are actually strong enough that they create secondary fields or signals when they encounter the outside of the equipment case or any other conductive or non-linear element. This is called the "saturation effect", and if it is not properly addressed can result in the cryptographic equipment put at risk of disclosing secrets. Typically the ambient RF environment near any cryptographic equipment should be well below -80 dBm and in some cases well below -110 dBm. Fields of this strength are common near broadcast facilities such as FM or television transmission towers or cellular/PCS towers. If you have a concern of this nature then you should contact a TSCM professional and schedule an evaluation of the RF in the vicinity of where you will be using your encryption equipment.
The critical thing to remember in all of this is that the ciphering key is where all the magic is at, and that the eavesdropper will typically target the ciphering circuit (or "Scrambler") to obtain the secret key. Sure they are interested in the material being scrambled by the cryptographic system, and they will also be interested in the inner workings of the phone, but it is obtaining the secret ciphering key that is most important to the spy. An encryption box or cryptographic device may only be classified secret, and yet the keying material is top secret, and the keying material is far more sensitive then the box itself, and must be protected with much greater care.
On a related note, it should be mentioned that the ciphering key is actually of a fairly small length, and that is even if a very small segment of it is compromised the eavesdropper's may be able to reconstruct it in whole (depending on what segment they get). In some cases even a 200 bit ciphering key can be broken by obtaining a small fragment the cipher which can be "snatched from the airwaves in less a ten millionth of a second" (if the cryptographic ignition key is loaded when in the presence of a cellular phone or strong RF field). Once the key is loaded into the cryptographic device the amount of time required to reconstruct the key is significantly larger, but not at all prohibitive. Remember, the eavesdropper is only looking for a few bits of data (the payload of the key), and that this small number of bits can be "hijacked" by an external RF source like a cellular phone as a highjack requires an absolute minimum of bandwidth.
Since the signal of interest is of extremely narrow bandwidth, and the "illuminating" signal can be easily correlated to the "signal of interest" the eavesdropper can be a considerable distance away from the encryption device and still perform the highjack (called "correlation gain", which can be well over 40 dB). This assumes that someone using the encryption device has a cell phone or other RF device on their person, that while not on an active call is still checking in with the base station for status updates on a regular basis. Without this "correlation gain" the intercept may only be feasible within a few feet, but with it; the eavesdropper can be 500 and even 1500 feet away.
Remember that the most valuable "item of interest" is not directly the clear text communication itself, but the key used to protect the communication. Once the eavesdropper has the key, then the communication itself would be targeted and exploited. You must protect the key at all times.
NEXTEL or Motorola iDen phones based on a TDMA or "Time Domain" signal presents a really nasty threat as the cell phone is constantly strobing a specific predictable time slice, and basically illuminates the STU and turns it into a strobing lighthouse that will seriously compromise classified information. If a NEXTEL is present within 12-15 feet of a STU-III (when it goes secure or a CIK is loaded) the phone and information passed though it should be considered compromised. The STU should always be located in an area called an exclusion zone, and cellular phones, pagers, beepers, and other RF devices should be kept outside of a stand-off zone of at least 15-20 feet (30 foot is good practice).
Now if this wasn't confusing enough; portable Inmarsat stations also present a similar problem, but only if the STU is located in front of the transmitter antenna or within the side lobes of the signal (about 45 degrees off the center axis of the antenna).
The best way to deal with this is to never have a cellular telephone or pager on your person when using a STU, or within a radius of at least thirty feet (in any direction) from an operational STU (even with a good ground). If the STU is being used in a SCIF or secure facility a cell phone is supposed to be an excluded item, but it is simply amazing how many government people (who know better) forget to turn off their phone before entering controlled areas and thus cause classified materials to be compromised.
Spook Hint: If you have a powered up NEXTEL on your belt and you walk within 12 feet of a STU-III in secure mode you have just compromised the classified key.
In the case where the STU is being used on a cell phone or satellite phone your best option is to keep the phone in analog mode (a STU, not a STE) and locate the STU a good 6-12 feet away from the antenna. In the case of an Inmarsat terminal simply keep the STU BEHIND the antenna by at least 10-15 feet (this is why Inmarsat terminals have long cables for the antenna). If you can obtain a digital Inmarsat connection you can get a very high quality connection, but the equipment is fairly costly, the terminal is quite large, and the digital service quite expensive.
At no time should a STU-III be operated in the presence of an RF field that exceeds -105 dBm for any signal with less then 30 kHz of occupied bandwidth. In the case of a signal which the occupied bandwidth exceeds 30 kHz the RF levels should not exceed -138 dBm.
On a final note; users of cryptographic equipment should be very careful and concerned where the encryption equipment is coming from, who makes it, and who handles it while in transit from the factory. This as call the "Equipment Pedigree", and all ciphering equipment should be handled in a special way to ensure that people are not tinkering with it after it leaves the factory.
In the case of corporate or government ciphering devices the equipment will normally be shipped right from the production line via courier directly to the customer, who will then store it under lock-and-key. In the case of a government client the shipment goes right from the production line to a central COMSEC depot via a special courier, where it is checked out before being issued for use in the field.
Encryption devices can be fairly easily compromised or "fiddled with" by adding in a few extra parts, or by swapping out the ciphering ignition keys to ones provided by the eavesdropper. There have actually been cases where a foreign government installed a small transmitter into the handset of a scrambled phone (of another government), or inserted a bypass device into the phone itself which allowed the spies to intercept the clear voice being scrambled by the phone. There have also been numerous cases where the intelligence agency of one nation "swapped the keys" of the diplomatic or military ciphers of one of their allies as the crypto was too strong, and poisoning the keys was far more efficient.
This is also why users of cryptographic devices need to change their cipher keys on a regular basis, and have the encryption equipment checked for modification, bugs, or compromising emanations periodically.
However, prior to the take-over AT&T dumped thousands of scrapped, used, and refurbished STU's into the salvage market. These nearly worthless scrap units then found their way into numerous spy shops and retail outlets who fraudulently peddled them as new products. Spy shops will often quote a price that is based on the older scrap units they bought a few years back, so ensure that if a price is quoted that it is for NEW equipment.
With this in mind you should only purchase secure communications equipment that is less then six months old. If you get a quote that seems a little "too good" or something seems fishy you would do well to ask some awkward questions.
Legitimate encryption products are not inexpensive or easy to obtain, and you can expect to pay several thousand dollars for even the most basic equipment.
![]()
|
To be contacted for a confidential consultation please E-mail: jmatk@tscm.com
or send a letter via US Mail to:
or call: URL: http://www.tscm.com/ |